
On Thursday 16 January 2020, I did a presentation on the “Privacy Aspects of ICT Projects” during a conference organised by the Data Protection Office of the Ministry of Technology, Communication and Innovation. A few days prior to the conference, while I was reflecting on what I was going to say, I had an intuition: Mauritius will have to undergo a profound digital transformation at all levels: government, companies, schools and individuals, if we want to attain Vision 2030.

This is why I decided to start my presentation by explaining to the audience what Vision 2030 means. I am always quite amazed, during the various talks I make, that only a few people know about this vision of the Government which was first mentioned by the then Prime Minister on 22 August 2015. Today, Vision 2030, which is about making Mauritius an inclusive high-income country well before 2030, is what dictates the various strategies and actions being done by Government.
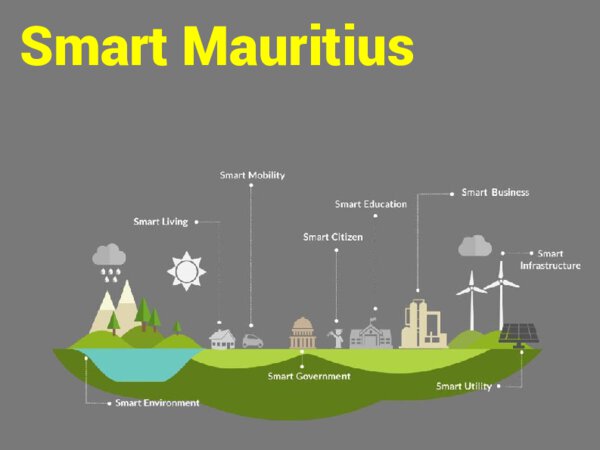
For me, the best way to be a high-income country and thus reach the status of Smart Mauritius is by our business entities, the conglomerates but also the SMEs including startups, getting more revenue. Given the limited size of the Mauritian market, this needs to be done through the development of new products and new services for new markets (especially the African market). This is why Government is investing massively in Smart Infrastructure, Smart Mobility and Smart Education, etc.
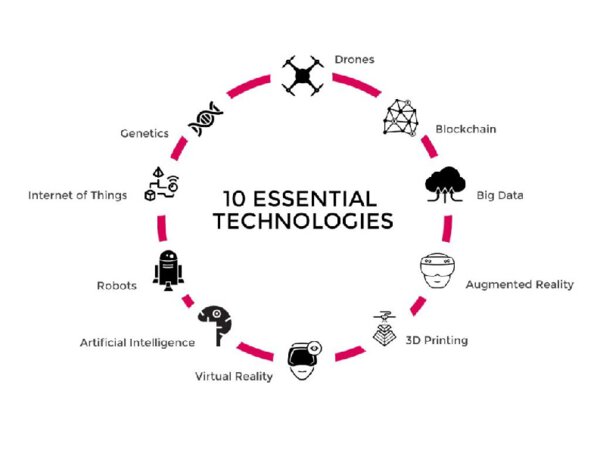
Now, to create new products and new services (in any field) and conquer new markets, one has to use technology to the full whether one requires a tried-and-trusted technology like Linux or the latest fashionable thing such as Artificial Intelligence.
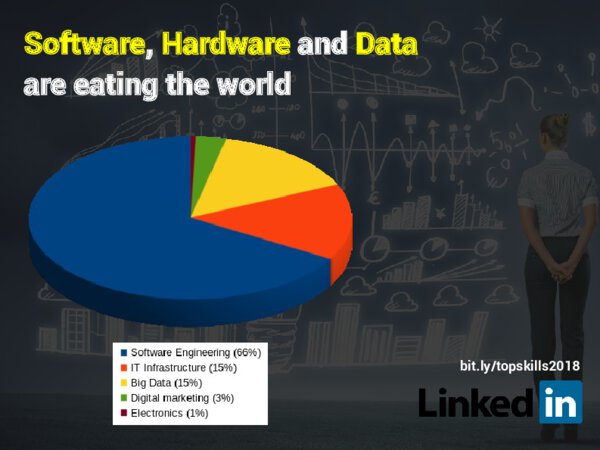
A lot of organisations have realised that technology in 2020 is about software. Software is eating the world after all. Our organisation, be it in Government or our companies, will have to either implement or develop software. It’s no wonder that 2/3 of the job offers on the LinkedIn website in 2018 were for software engineers (15% for IT people and 15% for data science people).
Now, the software needs to be trusted by all users, especially the ones giving their personal data. Therefore, making sure that the software respects the requirement of the Mauritian Data Protection Act or the European General Data Protection Regulations is key for the organisation to be trusted. Privacy has become so important that an organisation which acquires a reputation of not protecting the data of its clients or users is essentially moribund…

How can we implement or develop software which collects and processes personal data (as provided by users and clients) and which offers all guarantees that the privacy of the individual is going to be protected? This is quite a challenge and two technical avenues can be explored: computer security and information security.

Computer security is about the hardware and software aspects: making sure that the principle of security by design is followed from the very beginning (i.e. users only have to have access to the subset of data which they really require and this can be done through the principle of least privilege and proper access control). Then, security measures such as two-factor authentication, encryption, firewalls and intrusion detection mechanisms can be used to secure the infrastructure further. I am quite confident that using something like the Linux operating system for deployment is a great idea (ask Google, Amazon and Facebook!). Interestingly, the last time I used Windows for anything serious was around 2006, 14 years ago. Since then, I’ve been on Linux and macOS and I’m very happy. Of course, it is also important to train users to identify threats and to respond correctly when there is an incident.

I then spoke about information security which, interestingly, is more about the most vulnerable point in IT, the human. The best way to protect the information within an organisation is through the establishment of a good security policy (which needs to be fully understood and followed to the letter by all). It is also important to have physical security for the people and the equipment. This can be a challenge because people move. Laptops and smartphones today contain valuable information, and being so easy to steal, it is important to have a proper asset management system for business continuity. Of course, data needs to be protected (backups, mirroring, etc.) as well as the network.
Underlying everything is making sure that all layers, including all software, respect the requirements of laws such as our own Data Protection Act which mandates that users giving their data can also modify or erase the data afterwards. The law also mandates that the user be informed whenever his data is being collected so that he can give his consent or not. This is quite a challenge from a software development point of view.

Adhering to everything in computer security and in information security is quite difficult, costly and can be a lengthy process. But the reward is more trust and this is only way to get more business and, hence, more income and profit.
As I had been given 20 minutes for the presentation, I could not go into details in everything. I was telling a friend, after the presentation, that, if I was still at Knowledge Seven, I would have maybe created a 30 hour long training on this important topic.
By the way, I didn’t reinvent the wheel. A lot of my presentation was based on what I read online, most notably on Wikipedia which I love.
Thanks to everyone who came to the presentation and I hope you learned a few things. I definitely did while preparing it and doing it. Thanks to @yurit0s for the photo where I am visible.
